A Deep Dive into Modern Authentication
One-Time Passwords: The Security Game-Changer
In today’s rapidly evolving cybersecurity landscape, protecting sensitive data and digital identities has never been more crucial. One-time passwords (OTPs) have emerged as a reliable and effective method to enhance security across various applications, from email services to online banking. This blog delves into the intricacies of OTPs, covering their types, uses, benefits, and potential drawbacks.

Error: No videos found.
Make sure this is a valid channel ID and that the channel has videos available on youtube.com.
Understanding One-Time Passwords (OTPs)
A one-time password (OTP) is a security feature that generates a unique, temporary code for a specific transaction or login session. Unlike traditional static passwords that remain the same until changed, OTPs are dynamic and expire after a short period or after a single use, significantly reducing the risk of unauthorized access.
Types of One-Time Passwords
OTPs can be categorized based on their generation and delivery methods. The two primary types are:
1. Time-based One-Time Passwords (TOTP):
These OTPs are generated at regular intervals, typically every 30 to 60 seconds. The TOTP algorithms synchronize with the server's clock, ensuring the password can be validated within the time frame by both the client and the server.
2. HMAC-based One-Time Passwords (HOTP):
HOTPs are generated based on a counter that increments with each authentication request. Unlike TOTPs, HOTPs are not time-bound and remain valid until used, offering flexibility for situations where password entry timing may vary.
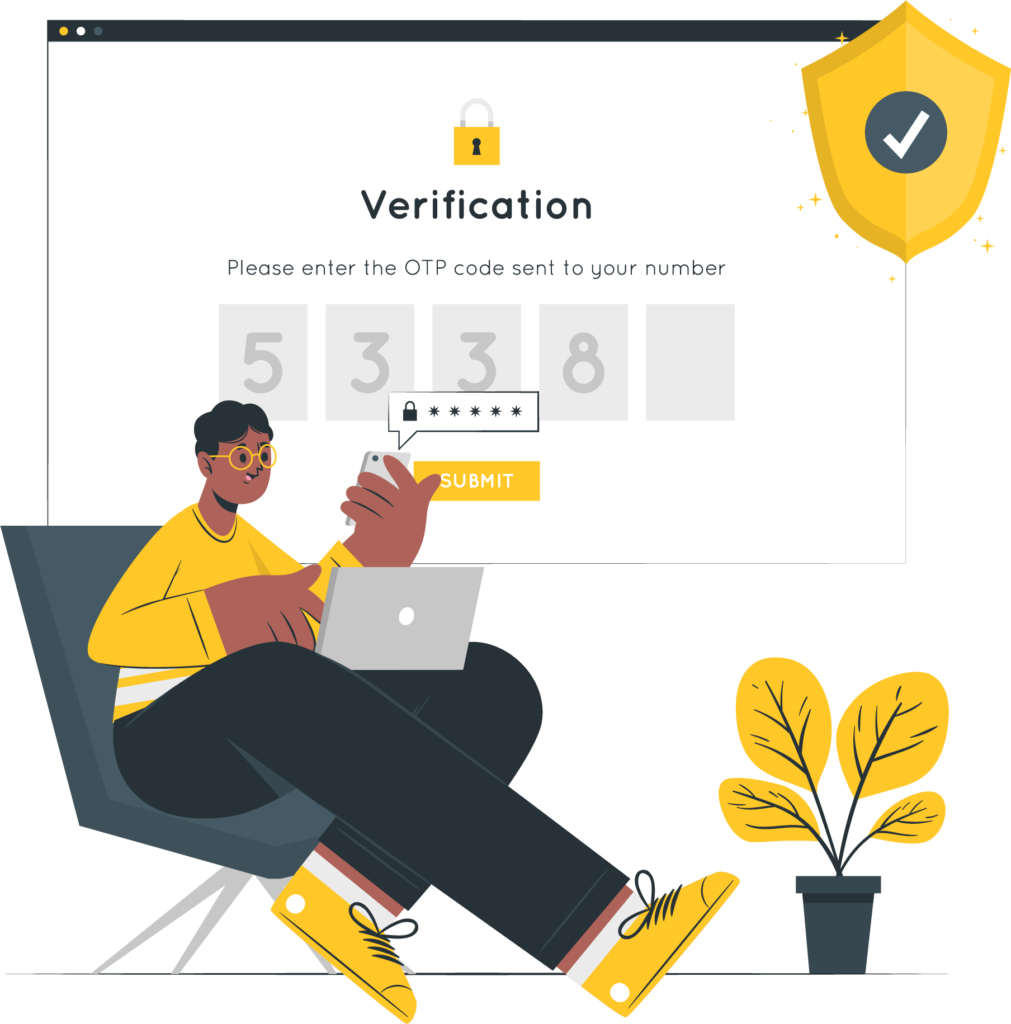
OTPs can be delivered through various channels, each with its own set of advantages:
- SMS: One of the most common delivery methods, particularly in banking and e-commerce. Users receive a code via SMS on their mobile phone, which they enter to complete the authentication process.
- Email: Similar to SMS, OTPs can be sent to a user’s email address. This method is often used as a backup when SMS delivery is not feasible.
- Authenticator Apps: Applications like Google Authenticator or Authy generate TOTPs on a user’s smartphone. These apps are preferred for their convenience and security, as they do not rely on potentially insecure SMS networks.
- Hardware Tokens: Dedicated hardware devices, often resembling key fobs, generate OTPs. These are commonly used in corporate environments for high-security access.
- Biometric Integration: Some systems combine OTPs with biometric data (e.g., fingerprint or facial recognition) for an additional layer of security.
OTPs are utilized across various domains to bolster security:
- Banking and Financial Services: OTPs add an extra layer of security to online banking transactions and credit card payments, protecting against fraud.
- Corporate Security: Businesses use OTPs for secure access to corporate networks and sensitive data, reducing the risk of unauthorized access.
- E-commerce: OTPs help verify user identities during online purchases, preventing fraudulent transactions.
- Email and Social Media: Platforms like Gmail and Facebook offer OTP-based two-factor authentication (2FA) to safeguard accounts against unauthorized access.
- Enhanced Security: OTPs provide superior protection against common threats like phishing, keylogging, and brute force attacks. Since the password is temporary and unique for each session, it is useless to attackers after its expiration.
- Convenience: OTPs, especially those generated by authenticator apps, offer a user-friendly way to implement two-factor authentication without the need for remembering complex passwords.
- Compliance: For industries regulated by stringent security standards (e.g., finance and healthcare), OTPs help in meeting compliance requirements for secure user authentication.
- Cost-Effective: Implementing OTPs, particularly via software solutions like authenticator apps, can be more cost-effective than deploying extensive hardware-based security measures.
- Delivery Reliability: OTPs sent via SMS or email can be delayed or intercepted, posing a risk to security and user experience. Relying solely on these methods can sometimes result in authentication failures.
- User Experience: While OTPs enhance security, they can also complicate the login process, potentially frustrating users. Balancing security and convenience is crucial for user adoption.
- Phishing Attacks: Sophisticated phishing attacks can trick users into revealing their OTPs. Educating users about recognizing and avoiding phishing attempts is essential.
- Synchronization Issues: For TOTP systems, time synchronization between the server and the client device is critical. Any discrepancies can lead to failed authentication attempts.
- Cost of Hardware Tokens: While effective, hardware tokens can be expensive to distribute and maintain, particularly for large organizations.
One-time passwords are a powerful tool in the modern cybersecurity arsenal, offering a flexible and secure means of authentication. By understanding the various types, delivery methods, applications, and potential challenges associated with OTPs, organizations and individuals can significantly enhance the security of their digital assets and sensitive data. As technology continues to advance, OTPs will play an increasingly vital role in safeguarding online interactions, ensuring that digital communications remain secure and trustworthy.
Securing Online Transactions with One-Time Passwords (OTPs)
In the digital age, online purchases have become a staple of everyday life. Whether you’re banking or shopping, the convenience is undeniable. However, this ease of access also brings increased vulnerability to fraud and cyber threats. One-Time Passwords (OTPs) have emerged as a powerful security tool to counter these risks. In this blog, we’ll explore how OTPs are implemented, their advantages, best practices, and how they enhance the security of online transactions.
Error: No videos found.
Make sure this is a valid channel ID and that the channel has videos available on youtube.com.
Implementation of OTPs in Online Transactions




Benefits of Using OTPs for Online Transactions
OTPs provide robust protection against common cyber threats such as phishing, keylogging, and brute force attacks. Even if a static password is compromised, the transaction cannot proceed without the OTP.
OTPs are particularly effective in preventing unauthorized transactions, as the code is sent directly to the user and is valid only for a short period.
Implementing OTPs increases user confidence in the security of online transactions, as they provide a visible and reliable layer of protection.
For industries like banking and finance, OTPs help meet regulatory requirements for secure authentication, protecting both the institution and its customers.
Challenges and Considerations
While OTPs significantly enhance security, there are some challenges and considerations to keep in mind:

- Delivery Delays: OTPs sent via SMS or email can sometimes be delayed, causing inconvenience to users. It’s important to ensure reliable delivery methods.
- User Experience: Adding an extra step in the transaction process improves security but can also complicate the user experience. Balancing security with ease of use is crucial.
- Phishing Attacks: Attackers may still attempt to trick users into revealing their OTPs through sophisticated phishing schemes. Educating users about these risks is essential.
- Cost: For businesses, the cost of implementing and maintaining an OTP system, especially one that relies on SMS, can be significant. Exploring cost-effective solutions like authenticator apps can help.
Best Practices for Using OTPs
To maximize the effectiveness of OTPs in securing online transactions, consider the following best practices:
1. Multi-Channel Delivery:
Offer multiple OTP delivery methods (SMS, email, authenticator apps) to ensure users have reliable access.
2. User Education:
Educate users about the importance of OTPs, how they work, and how to recognize phishing attempts.
3. Regular Audits:
Conduct regular security audits to ensure the OTP system is functioning correctly and securely.
4. Fallback Options:
Provide fallback authentication options in case users cannot receive their OTPs, such as security questions or backup codes.
Error: No videos found.
Make sure this is a valid channel ID and that the channel has videos available on youtube.com.
Conclusion
With the increasing prevalence of online transactions and the ever-changing nature of cyber threats, One-Time Passwords (OTPs) provide a strong defense against security breaches. By understanding how OTPs work, implementing them effectively, and following best practices, businesses and individuals can protect their online transactions from fraud and unauthorized access. As technology continues to evolve, OTPs will play an increasingly vital role in safeguarding digital interactions, becoming a cornerstone of cybersecurity strategies.